These days I’m receiving more requests for help than ever. Most of them refer to suspicious emails, maybe because people are more aware, maybe because the current geopolitical situation is evolving fast.
Any password policy, even with strict rules, can be easily bypassed with simple tricks: Passw0rd!, Passw0rd$, Password!1 can be all valid passwords for length and complexity. In this common scenario it’s useful to regularly audit Active Directory passwords against password dictionaries (like RockYou) and/or HaveIBeenPwned .
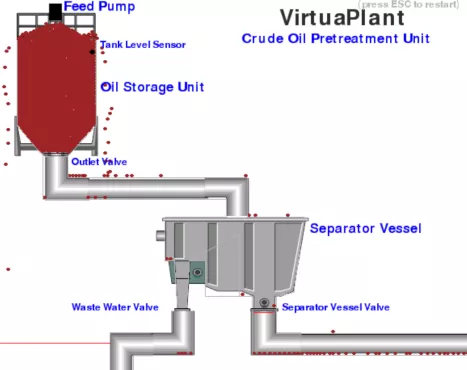
This post explore my second TryHackMe room: Attacking ICS Plant #2 . Because the VM can be unresponsive, I also provide the OVA for offline labs. The room allows attacking a simulated refinery plant, gaining basic knowledge on ICS protocol weakness.
This post explore my first TryHackMe room: Attacking ICS Plant #1 . Because the VM can be unresponsive, I also provide the OVA for offline labs. The room allows exploration of a simulated bottle-filling plant, gaining basic knowledge on ICS protocol weakness.
On my home Linux box, I implemented Let’s Encrypt to properly manage secure HTTPs connections. To properly configure it we need to: Make the directory /.well-known reachable via HTTP and mapped locally under /var/www/html/.
Many companies rely on RFID (Radio-frequency identification) tags for many aspects. Employer badges are often RFID-based and allow for unique identification, authorization, and account for each employer. Other companies use simple RFID tags or the more evolved NFC smartcards to identify and bill for services.
Every time I need to work with Linux SNMP utilities, I have to re-learn some commands. This post summarizes useful SNMP commands for anyone who needs a reference guide. Common options Usually, I need to build a custom and trusted MIB repository.
Firejail is a powerful tool that can be used to sandbox a lot of applications. By default, Firejail provides profiles for Chrome, Firefox, Telegram, and other famous applications. Wireshark is still missing.
VRF (Virtual Routing and Forwarding) allows having multiple and separated routing tables on the same system. On Linux, VRF support has been started on 4.3 kernels. Ubuntu 16.04 brings 4.4 kernels but mind that 4.