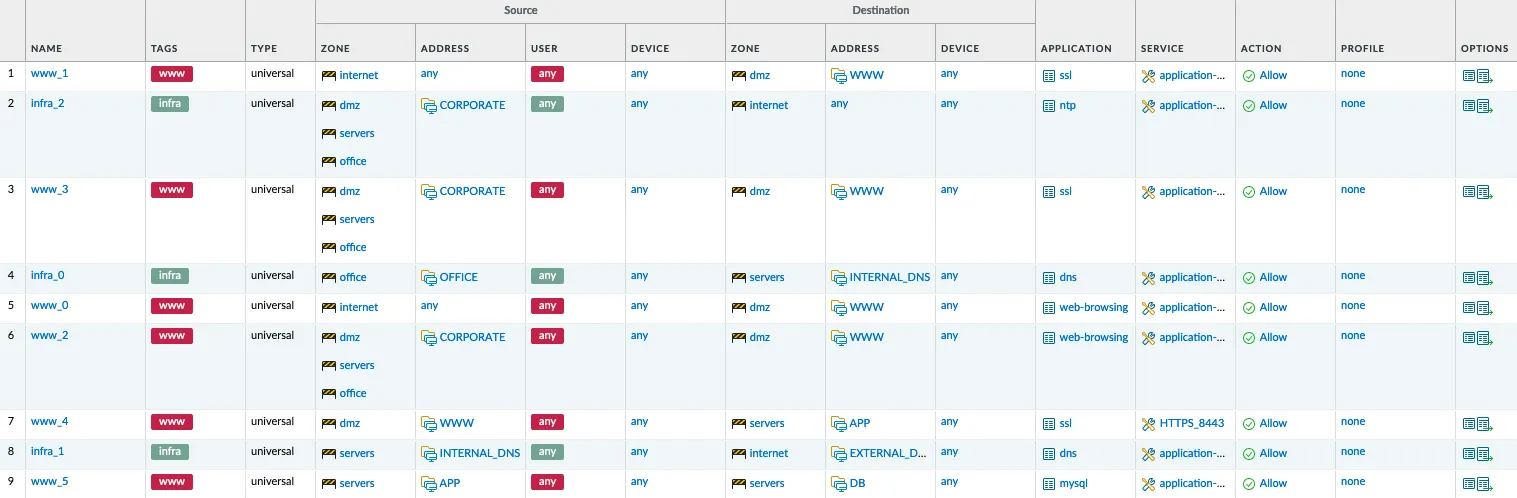
It has been about 6 years since the Automate IT² event organized by me and Gabriele Gerbino. During the event, Xavier Homes presented a case that fascinated me. Today we might call it: Firewall as Code.
Web Archive is an online service (non-profit) that has long been recording various websites by archiving them in a virtually permanent manner so that anyone can analyze the history and changes of a specific website.
I couldn’t find a suitable title for this post, in which I try to gather various insights that I’ve received in the past few days and that I’ve planned, sooner or later, to discuss together with Rocco Sicilia.
In recent years, Network Access Control (NAC) solutions based on the 802.1x protocol have gained significant traction. Like all security solutions, it is crucial to carefully evaluate their functionality to integrate them into a proper Cybersecurity strategy.
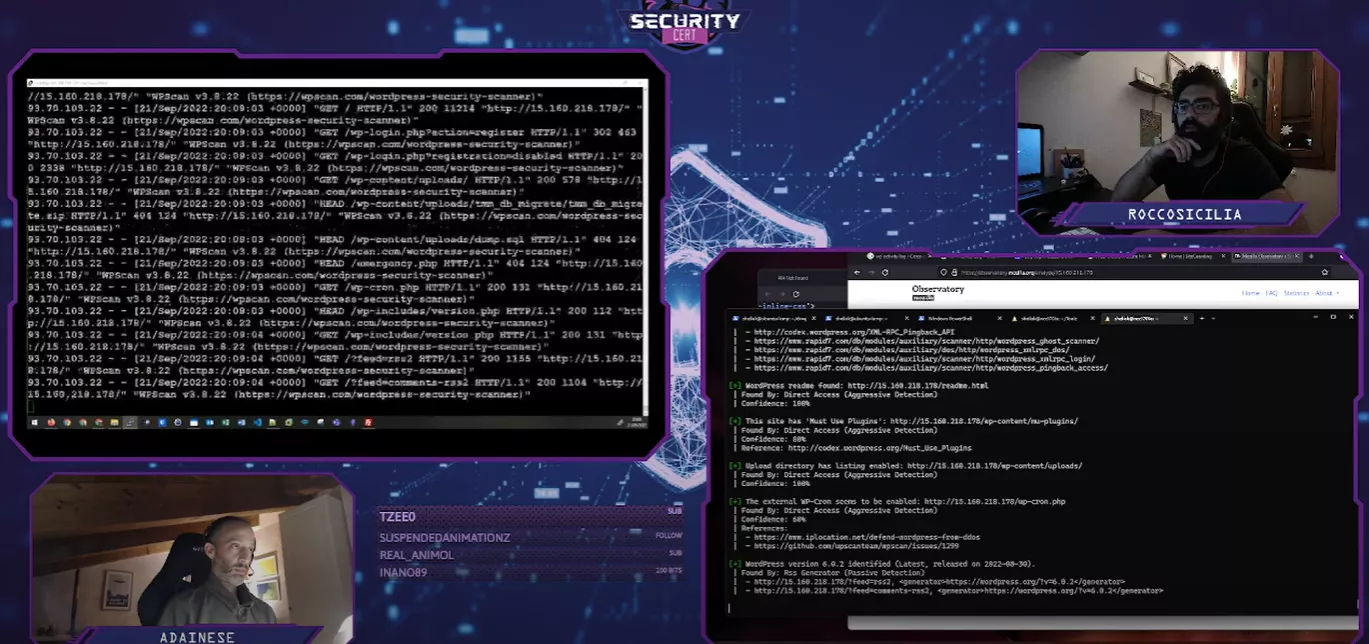
During the last “Blue Vs Red” events, together with Rocco Sicilia , we discussed how to attack and defend a simple, all-in-one, WordPress site. This post serves as a memorandum to remember all topics we discussed and how we reacted to specific attacks.
I always need to set critical environment variables on my Bash (API tokens), and of course, it’s a very bad idea to store them on .bashrc. I found a simple way to store them in an encrypted file loading it only when necessary:
Security assessments are part of my daily job, and automation is part of my mindset. CIS Controls provides a set of standard controls that should be checked on… anything. To be specific CIS also provides a benchmark (a sort of step-by-step guide) for many environments.
I’m discussing the IEC 62443 certification with an organization: that build and sell ICS plants which are risky from a safety perspective. They currently comply with the Machinery Directive (Directive 2006/42/EC of the European Parliament), but they are not considering the Cyber risk.
A few months ago a customer asked me about how to integrate custom applications and SIEM. The customer developed a Java application using a Tomcat container and the question came from an insurance company.
As you probably know, I’m working on learning simulated lab for years. In the last couple of years, I moved to OT/ICS Cybersecurity, and sometimes I need a realistic lab to show the consequence of a Cyberattack targeting OT/ICS devices.