For several years now, Ansible AWX has been on my ToDo list. I have always postponed dealing with it due to its complexity, but today I find myself having to tackle it.
In recent years, Network Access Control (NAC) solutions based on the 802.1x protocol have gained significant traction. Like all security solutions, it is crucial to carefully evaluate their functionality to integrate them into a proper Cybersecurity strategy.
Operating on a data center (DC) or backbone Internet Service Provider (ISP) typically involves a significant amount of human effort, resulting in operational costs that are often overlooked. However, these costs can be optimized by harnessing the power of automation to handle simple and repetitive tasks efficiently.
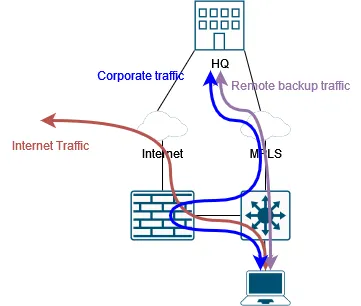
I used to deploy a simple network architecture for two main reasons. They are easy to debug/troubleshoot Engineers who came after can easily understand and manage them. With these rules in mind, I usually deploy in-line firewalls, meaning that traffic is routed through a firewall that is placed “in the path”:
A few months ago I had a chat with a customer about IAAS. The customer wanted to change its business model from an internal ICT only, to an IAAS style ICT, for both internal and external users.
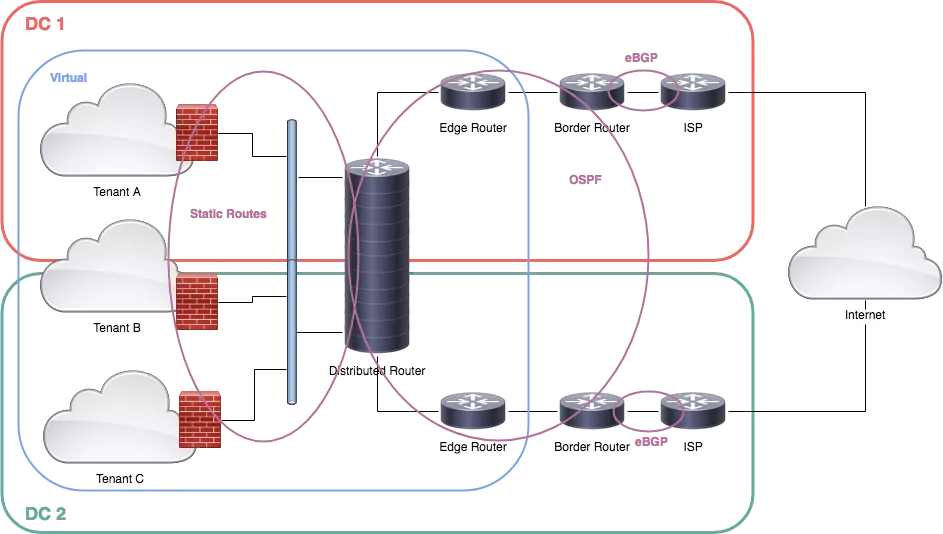
IT infrastructures are evolving fast and they are not becoming simpler. The more flexibility is requested from the application layer, the more complexity is added to the network layer. From RFC1925:
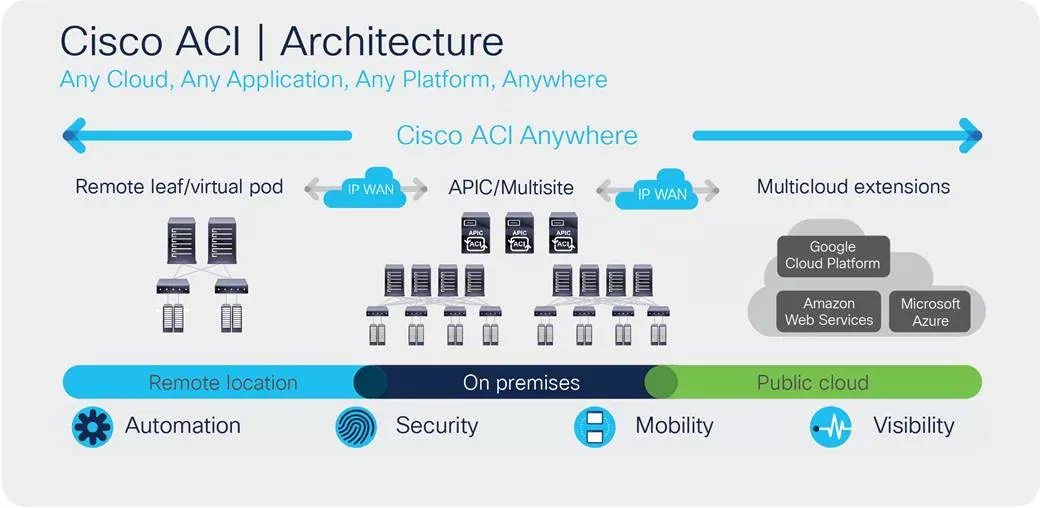
We all know that Google, Fastly, and Facebook… are defining networks as a software (yes, SDN, but the real Software Defined Network) using custom tools. But what exactly does SDN mean?
In this case, the application team is reporting a random high RTT between a client and a server. Both client and server are Linux virtual machines, under VMware vSphere, and the path is through a lot of firewalls, routers, switches, load balancers… and so on.
A not-so-easy process about QoS involves the verification of end-to-end QoS marking: are the marks maintained through the all network? Before going deep, let’s recap how an IP packet can be marked:
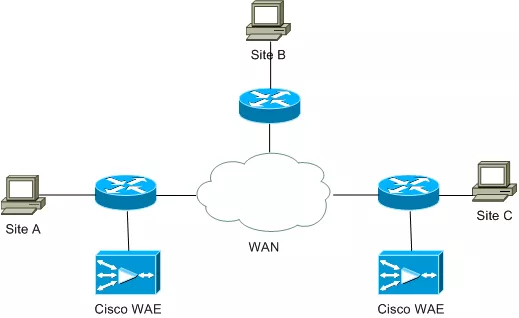
The Cisco WAAS system consists of a set of devices that work together to optimize TCP network traffic. There are two types of devices that run WAAS software: Cisco Wide Area Application Engine (WAE) Cisco Wide Area Virtualization Engine (WAVE) WAVE appliances implement virtualization: virtual blades can run one or more virtualized OSes within the WAVE appliance.