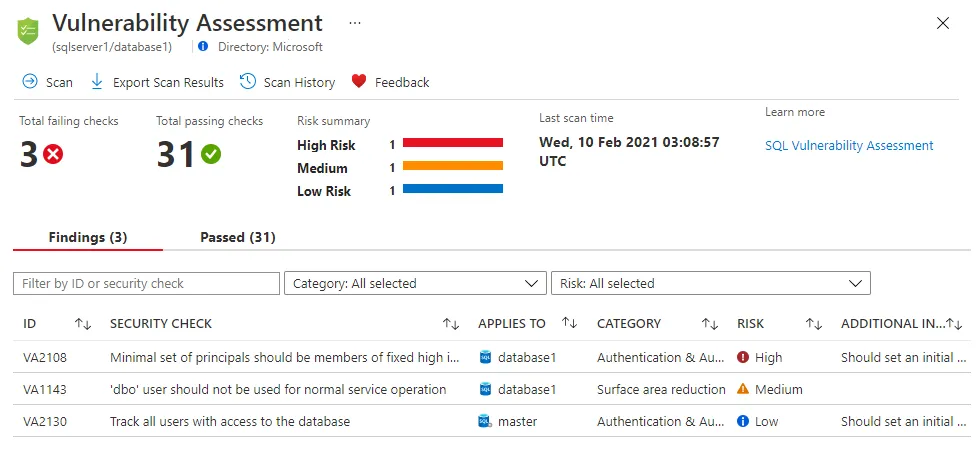
In this article, I’m explaining why we are executing VA, why the traditional approach is dangerous and how we should manage the risk bound to vulnerabilities. I’m also discussing a few false myths about VA.
Nowadays (hopefully) all companies are executing regular vulnerability assessments. They often use different partners/tools each year and they often limit themselves to vulnerability assessments. VAs are not the end of a security strategy, they are just a small step at the beginning.
A few days ago, together with Rocco Sicilia and FESTO Academy , I presented a webinar on OT/ICS Cybersecurity approach. We are often spending time increasing Cybersecurity awareness, and that webinar was focused to gives Cybersecurity fundamentals to OT managers.
We’re leaving in the ‘hype’ era, where everything is sold as the Holy Grail for a non-real problem. Let’s try to analyze things with a critical eye. Pushed by a friend, who is writing a couple of very good posts I recommend, I’m now sharing my thoughts about automation, the future of network engineers, AI, and so on.