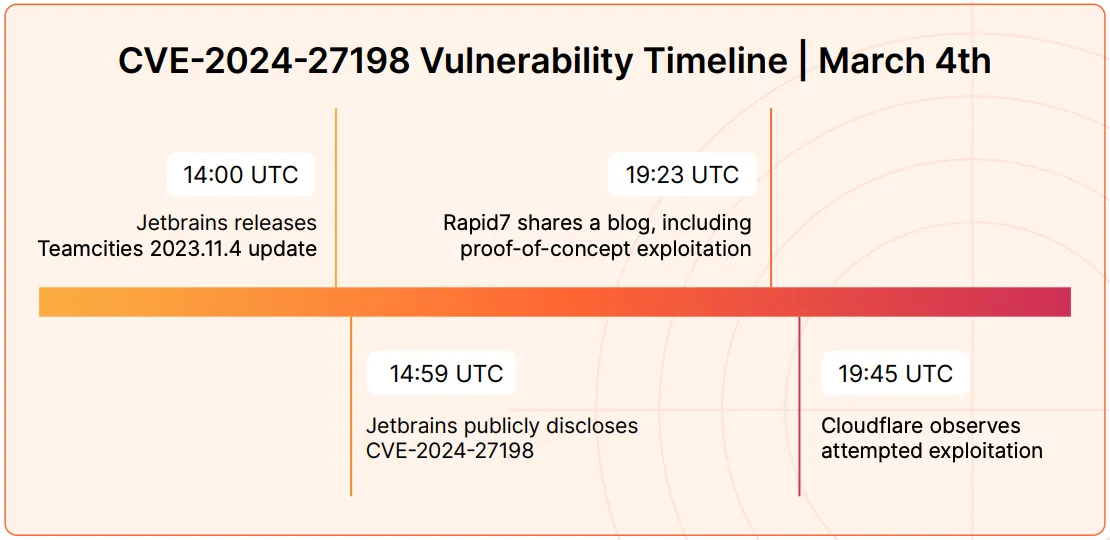
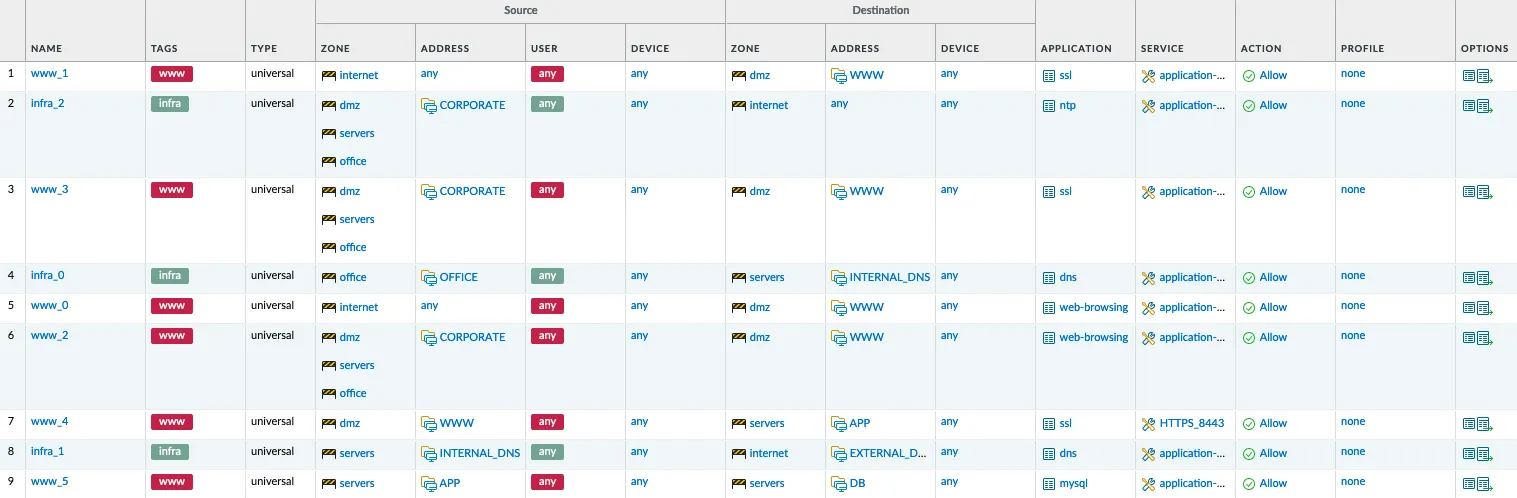
A lot has already been said about Vulnerability Management (VM), and I’ve personally touched on this topic several times before. Yet, the reality is that managing vulnerabilities remains a significant challenge for most organizations.
There is much discussion around Zero Trust Architecture (ZTA), but it seems the concept of Assume Breach Design has yet to be formalized. Or, at least, a Google search does not yield results.
It’s time to revisit the ICS/OT world, as it has unique characteristics that influence its processes and tools. First, I would categorize this broad field into the following groups: Systems localized within a confined area (e.
It has been about 6 years since the Automate IT² event organized by me and Gabriele Gerbino. During the event, Xavier Homes presented a case that fascinated me. Today we might call it: Firewall as Code.
This book originates from the authors’ experience in conducting security incident simulations within companies. The scenarios described are always based on real cases, modified to make them unrecognizable while still usable as tabletop exercises.
Web Archive is an online service (non-profit) that has long been recording various websites by archiving them in a virtually permanent manner so that anyone can analyze the history and changes of a specific website.
I couldn’t find a suitable title for this post, in which I try to gather various insights that I’ve received in the past few days and that I’ve planned, sooner or later, to discuss together with Rocco Sicilia.
I’m discussing the IEC 62443 certification with an organization: that build and sell ICS plants which are risky from a safety perspective. They currently comply with the Machinery Directive (Directive 2006/42/EC of the European Parliament), but they are not considering the Cyber risk.
Managing Cybersecurity is expensive, we all know that. But not managing it is also more expensive. Given my experience, an SME recovers from a critical Cyberattack in 5-10 days, if it can recover (yes I also personally know companies that lost everything because of a Cyberattack).
Many companies (hopefully) are collecting logs in a central system. The reason besides that is for compliance and sometimes for root cause analysis. In this post, I want to recap that log management is not just about log collections, and why and how the process should be designed.