Following an idea of Micheal Bazzel , I decided to write a short procedure to remove unwanted software from Android smartphones. It’s not only about cleaning the phone, it’s about privacy.
I’m discussing the IEC 62443 certification with an organization: that build and sell ICS plants which are risky from a safety perspective. They currently comply with the Machinery Directive (Directive 2006/42/EC of the European Parliament), but they are not considering the Cyber risk.
Managing Cybersecurity is expensive, we all know that. But not managing it is also more expensive. Given my experience, an SME recovers from a critical Cyberattack in 5-10 days, if it can recover (yes I also personally know companies that lost everything because of a Cyberattack).
Many companies (hopefully) are collecting logs in a central system. The reason besides that is for compliance and sometimes for root cause analysis. In this post, I want to recap that log management is not just about log collections, and why and how the process should be designed.
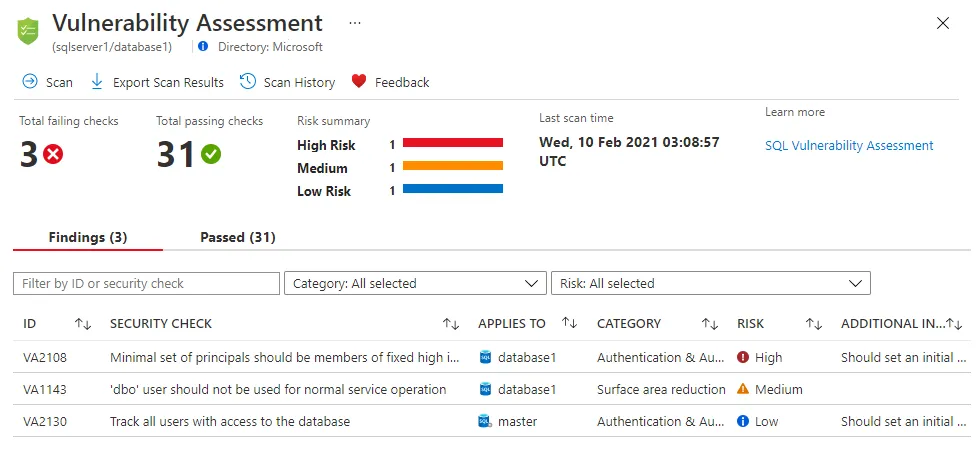
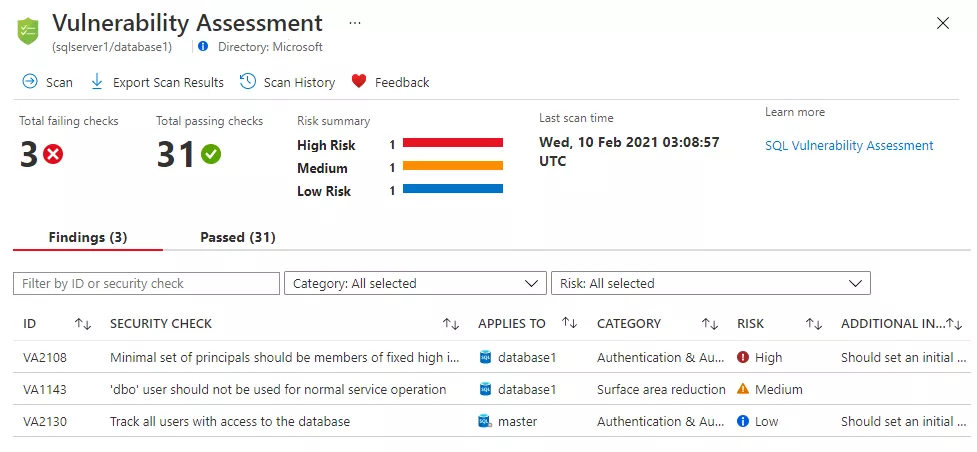
In this article, I’m explaining why we are executing VA, why the traditional approach is dangerous and how we should manage the risk bound to vulnerabilities. I’m also discussing a few false myths about VA.
In the last few years, I started to work (pro bono) on a different topic: personal digital security. In this post, I want to discuss post-mortem security: how to minimize family threats after death.
My previous post about the UNetLab story become unexpectedly popular. UNetLab has been one of my most important and public projects, and I’m honored so many people all around the world used my homemade project.
A few months ago a customer asked me about how to integrate custom applications and SIEM. The customer developed a Java application using a Tomcat container and the question came from an insurance company.
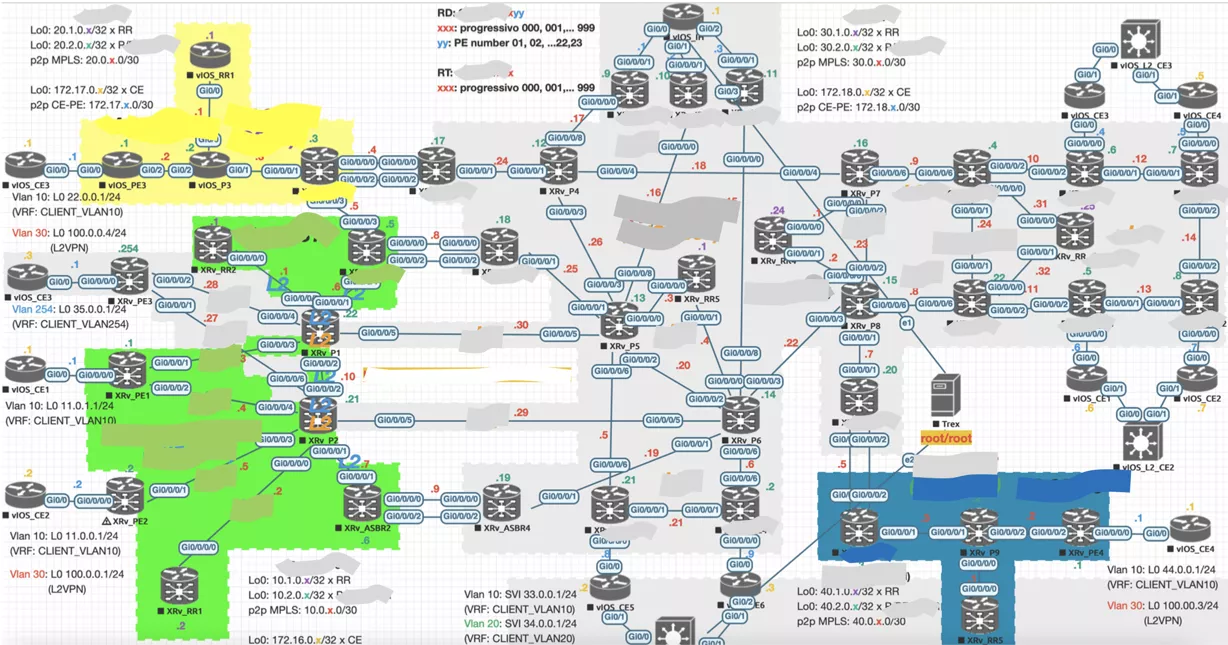
As you probably know, I’m working on learning simulated lab for years. In the last couple of years, I moved to OT/ICS Cybersecurity, and sometimes I need a realistic lab to show the consequence of a Cyberattack targeting OT/ICS devices.
Nowadays (hopefully) all companies are executing regular vulnerability assessments. They often use different partners/tools each year and they often limit themselves to vulnerability assessments. VAs are not the end of a security strategy, they are just a small step at the beginning.