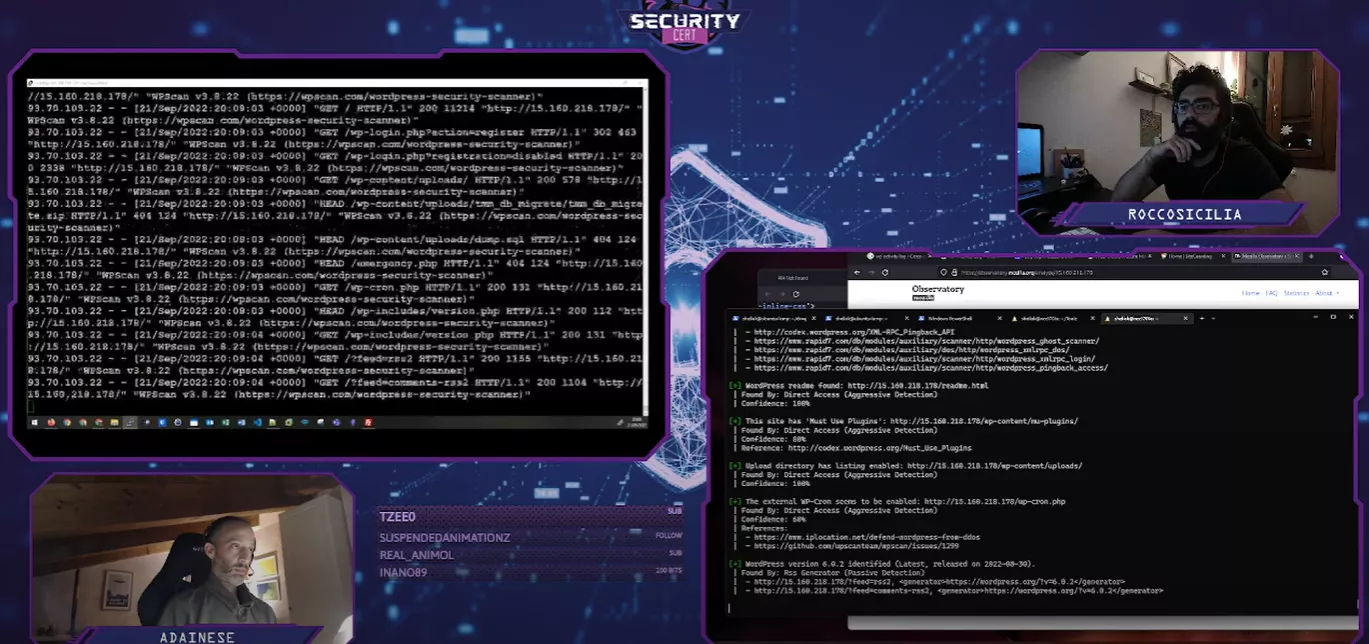
During the last “Blue Vs Red” events, together with Rocco Sicilia , we discussed how to attack and defend a simple, all-in-one, WordPress site. This post serves as a memorandum to remember all topics we discussed and how we reacted to specific attacks.
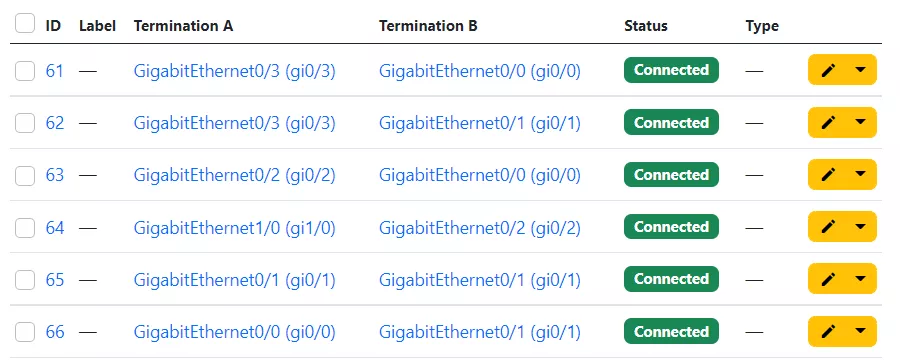
Years ago I worked on a data center migration project. I was in charge to review network documentation, and automating the configuration, testing, and migration phases. There is no chance to review dozens of switches manually, so I wrote some Python scripts to get neighborship and configuration from switches, drawing Visio diagrams.
I always need to set critical environment variables on my Bash (API tokens), and of course, it’s a very bad idea to store them on .bashrc. I found a simple way to store them in an encrypted file loading it only when necessary:
A few days ago, my daughter has deleted by mistake some photos on her camera. It has been 10 years at least since I recovered deleted files last time, so I had to find out how to approach the problem in 2022 with Kali Linux.
During security assessment on Smarthome applications, I usually need to analyze encrypted HTTPS communications. Applications usually check for valid certificates, but also check that certificates are signed by a specific issuer.
As private individuals we are using a lot of consumer IoT devices: almost any standard home equipment can now be remotely controlled by a specific application installed on a smartphone.
I usually don’t write about OSINT techniques, I think that before approaching OSINT we should speak about ethics and respect. By the way, some OSINT automation techniques are harmless: if you don’t know what you have to search for, you won’t be able to get anything regardless you are automating or not.
Security assessments are part of my daily job, and automation is part of my mindset. CIS Controls provides a set of standard controls that should be checked on… anything. To be specific CIS also provides a benchmark (a sort of step-by-step guide) for many environments.
I have a “landline” VoIP number, used by my parents to reach me when my phone is turned off. Apparently, landlines number are preferred by spammers, so I wrote a simple firewall zero-trust configuration for my FRITZ!
I had an interesting chat with a friend: he was reporting to me that his photovoltaic management app wasn’t working anymore. The vendor upgraded the Cloud API breaking compatibility with older products.