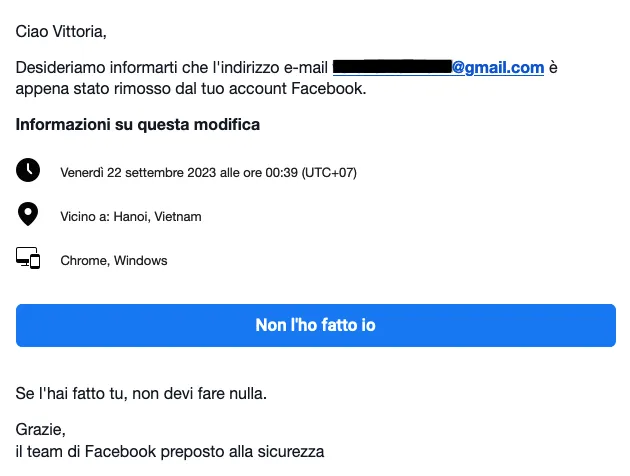
This is the story of Vittoria (a pseudonym, henceforth referred to as V). A few days ago, V called me in an emergency: her Facebook account had been stolen by Nhang (a pseudonym, henceforth referred to as N).
In this article, we present an initial example of executing mass commands using Ansible on Cisco IOS devices. We will utilize the pre-configured “Cisco Legacy Core-Access topology” lab available in the repository DevNetOps course material:
Ansible is distributed as a Python module installable via PIP. The installation process is straightforward but warrants some considerations. Typically, the automation host, the system from which all automation scripts originate, is one of the most critical systems within an infrastructure.
The first step to work in the IT field today is to set up a laboratory. EVE-NG (formerly UNetLab) can be used for network, network security, and automation labs. EVE-NG is based on Ubuntu Linux 20.
This post recounts an attempt at fraud via SMS and voice call with a fake voice, targeting an elderly person. Although this type of fraud is not new, the way it was executed deserves further examination.
Operating on a data center (DC) or backbone Internet Service Provider (ISP) typically involves a significant amount of human effort, resulting in operational costs that are often overlooked. However, these costs can be optimized by harnessing the power of automation to handle simple and repetitive tasks efficiently.
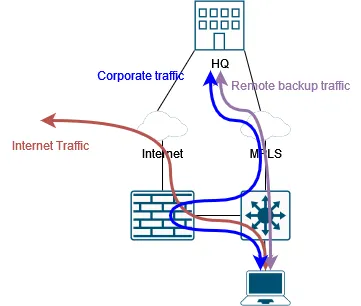
I used to deploy a simple network architecture for two main reasons. They are easy to debug/troubleshoot Engineers who came after can easily understand and manage them. With these rules in mind, I usually deploy in-line firewalls, meaning that traffic is routed through a firewall that is placed “in the path”:
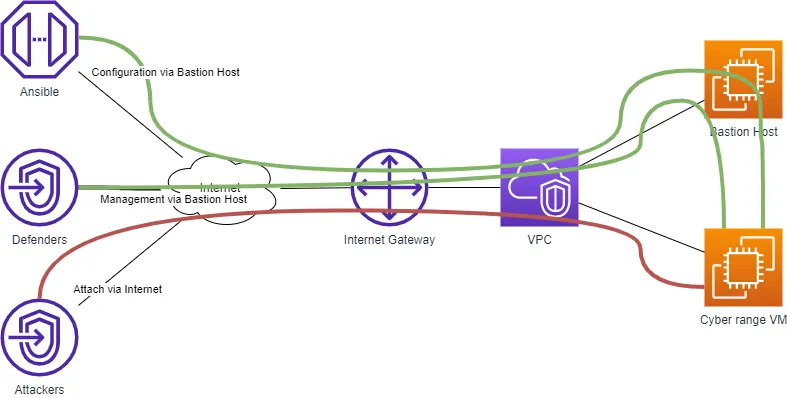
This is the third part of my IaC overview based on a personal experiment: building Cyber range using the IaC paradigm. Here is the first and second parts. A few weeks ago I met Spacelift and I had the chance to test their product.
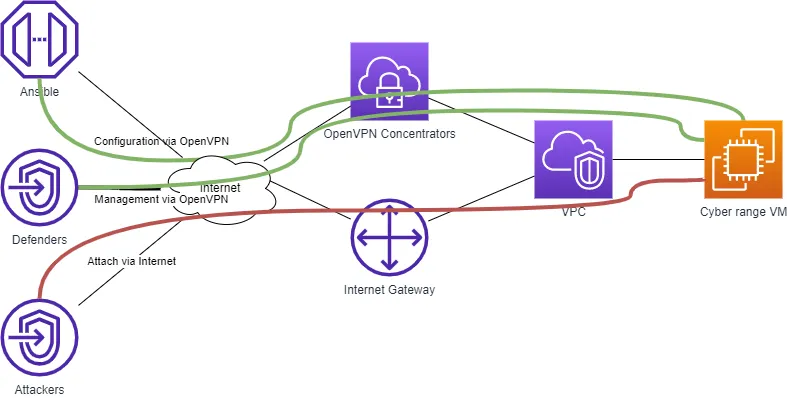
This is the second part of my IaC overview based on a personal experiment: building Cyber range using the IaC paradigm. Here are the first and third parts. In a pure design perspective, the client-to-site VPN approach is still the best.
This is the first part of my IaC overview based on a personal experiment: building Cyber range using the IaC paradigm. Here are the second and third parts. During my Twitch session, I’m used to offering a practical lab to attendees.