Welcome to our series focused on Ansible Automation! In this comprehensive series, we’ll delve into Ansible, an incredibly powerful tool designed to automate a wide range of IT tasks and streamline the management of complex deployments.
Join me as I embark on an exciting journey to develop UNetLab v3! On this Patreon series, you’ll get an exclusive behind-the-scenes look at the evolution of UNetLab, from initial concepts to advanced configurations.
Welcome to our Patreon-exclusive series on Nautobot Automations! If you’re an IT professional, network engineer, or automation enthusiast, this is your gateway to mastering network automation using Nautobot. Nautobot is an open-source Network Source of Truth and Network Automation Platform.
It has been about 6 years since the Automate IT² event organized by me and Gabriele Gerbino. During the event, Xavier Homes presented a case that fascinated me. Today we might call it: Firewall as Code.
This book originates from the authors’ experience in conducting security incident simulations within companies. The scenarios described are always based on real cases, modified to make them unrecognizable while still usable as tabletop exercises.
For several years now, Ansible AWX has been on my ToDo list. I have always postponed dealing with it due to its complexity, but today I find myself having to tackle it.
Web Archive is an online service (non-profit) that has long been recording various websites by archiving them in a virtually permanent manner so that anyone can analyze the history and changes of a specific website.
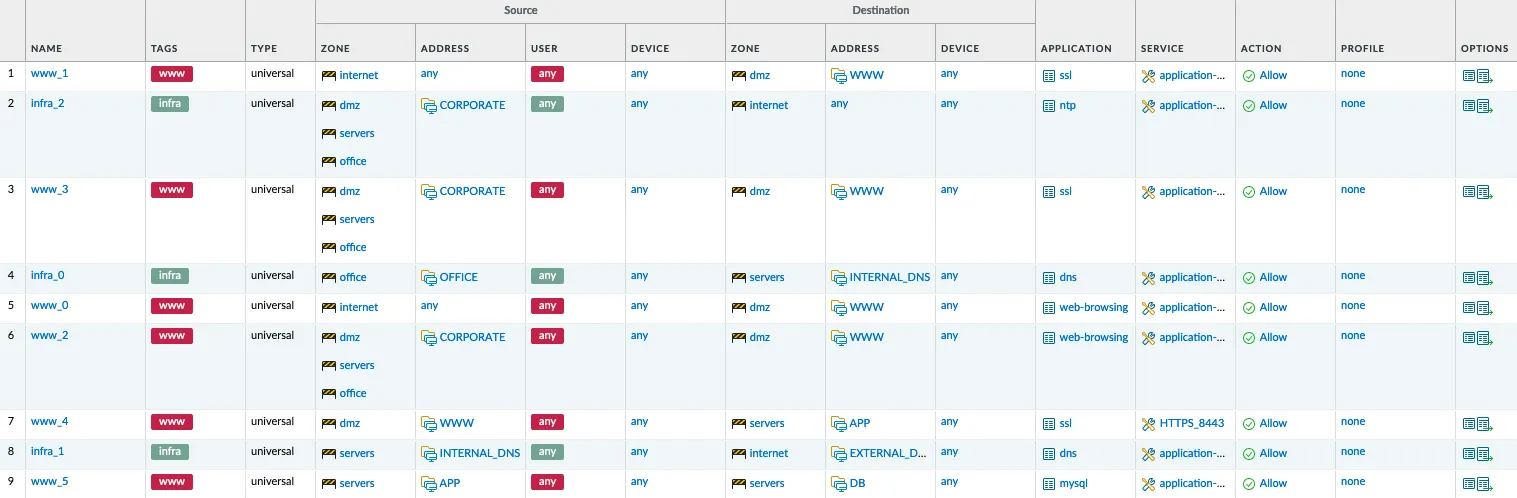
Network automation arises as a necessity to reduce and enhance operability, standardize working methods, and operate on multiple devices in significantly reduced times. The number of individuals interested in this approach is steadily expanding: starting from network engineer teams, automation is now attracting GRC (Governance Risk and Compliance) teams.
Alright, here’s how I got back into (loving) the cold, and why I did it. Normally, I don’t spill much about my personal life, but I figured, hey, even this is a form of hacking: hacking oneself.
Developing automations that interact with network devices requires having a development environment to test, learn, and experiment with frameworks, integrations, and automations. Virtualization over the years has allowed anyone to have realistic copies of network devices at their disposal.