EVE-NG Linux VM SSH troubleshooting
September 20, 2025
Automating Palo Alto Firewall via XML API
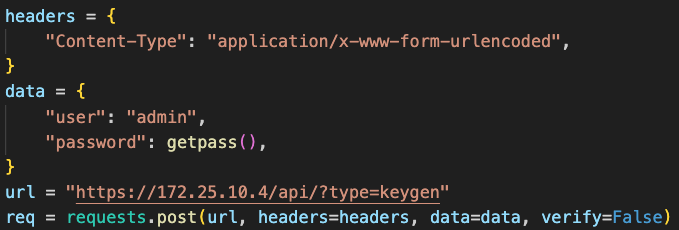
Palo Alto Networks firewalls provide XML-based APIs for interacting with the system. To use the API, the first step is to generate an API key that will authenticate our requests:
curl -k -H "Content-Type: application/x-www-form-urlencoded" -X POST https://firewall/api/?type=keygen -d 'user=admin&password=password'
Alternatively, a simple Python script can be used:
At this point, we can use the XML API to perform any operation typically executed via the web interface or CLI. The token must be passed as a GET parameter in every API request. Documentation is available directly on the firewall at: https://172.25.10.4/php/rest/browse.php
The script is available in the GitHub repository .
Operational Commands via XML API
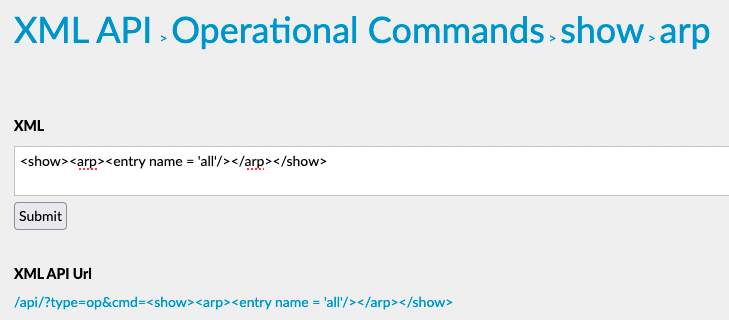
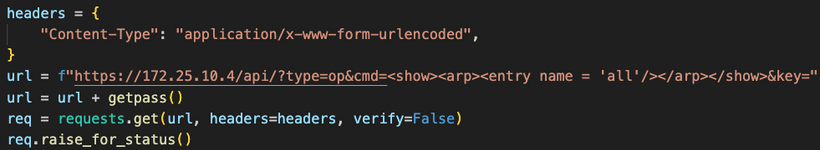
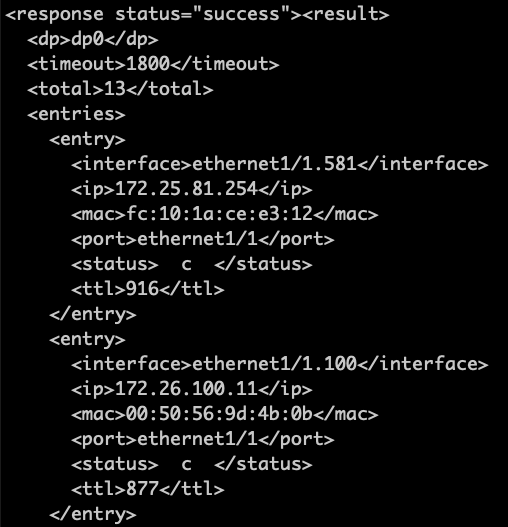
Let’s revisit the example from the previous post and retrieve the ARP table. Documentation provides the XML call to execute: https://172.25.10.4/php/rest/browse.php/op::show::arp
The script is straightforward:
The output is the ARP table in XML format:
XML is not the most Python-friendly format. The official documentation warns about various risks:
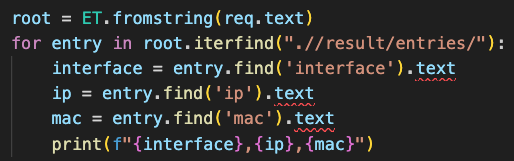
However, we can treat the XML output from the firewall as trusted and proceed using the ElementTree library .
Compared to JSON, navigating XML requires more experience. The example below shows how to extract data from the XML response returned by the firewall:
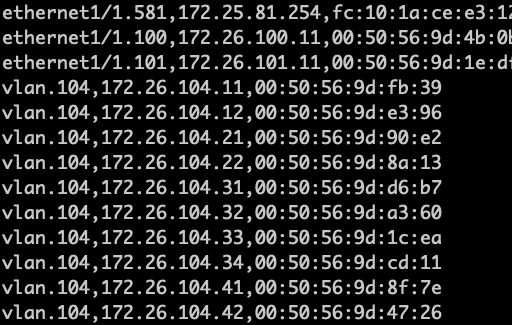
The script output is similar to the following:
Continue reading the post on Patreon .