EVE-NG Linux VM SSH troubleshooting
September 20, 2025
Automating Palo Alto Firewall via CLI
The first method we will discuss is called screen scraping, a topic already covered in the past. We use the screen scraping approach when automating devices that are designed to be managed via CLI, without APIs that allow us to cover all the scenarios we are interested in. Screen scraping is commonly used when dealing with network devices.
As we will see later, Palo Alto Networks firewalls offer XML-based APIs that make the screen scraping approach less attractive unless for very specific cases.
For Palo Alto Networks firewalls, screen scraping can be useful for performing specific actions related to monitoring and troubleshooting.
Let’s look at a couple of examples.
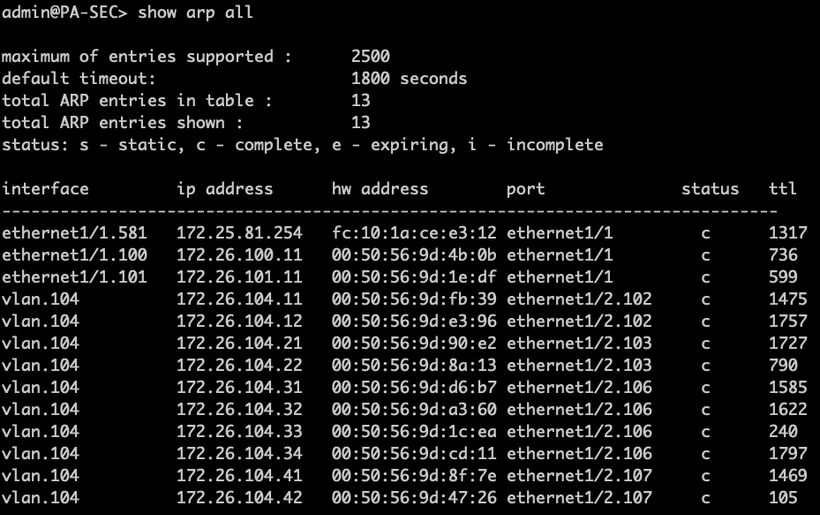
The first example is a request from a client several years ago. The client wanted to implement a device locator that would allow them to identify the location of a device based on its MAC address or IP address. It was necessary to gather the MAC address table and the ARP table from all devices. For the ARP table, we needed to retrieve the output of the show arp all command and convert it into machine-readable format (parsing): this is screen scraping.
We will use two tools:
- netmiko to connect to the devices, execute the command, and collect the output.
- NTC Templates to transform the output into JSON format.
Continue reading the post on Patreon .