EVE-NG Linux VM SSH troubleshooting
September 20, 2025
Industrial network segmentation with Private VLANs
We have explored how to transparently segment an OT/ICS network into groups using VLAN Insertion from Palo Alto Networks. The flexibility of this feature has allowed us to divide our lab environments into groups without the need to reconfigure IP addresses. Additionally, this solution enables us to define policies to allow specific communications between groups when necessary.
Since the early 2000s, a standard feature has been available to achieve a similar outcome: Private VLAN, also known as port isolation, which allows devices to be segmented into port groups.
Private VLAN
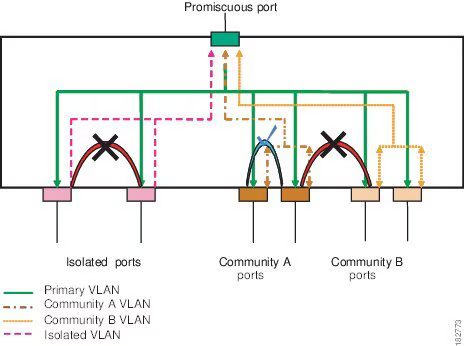
Private VLANs are defined in RFC5517 as VLAN-based “forced forwarding.” In other words, frame forwarding is determined at the VLAN level.
Two types of VLANs are defined:
- Primary VLAN: This VLAN handles traffic common to all groups.
- Secondary VLAN: This VLAN is associated with port groups and can be either Isolated or Community. In an Isolated VLAN, each port can communicate only with the primary VLAN. In a Community VLAN, each port can communicate with the primary VLAN and all ports within the same Community VLAN.
There are three types of ports:
- Promiscuous Access Port (P-Port): This port can communicate with any other port, regardless of VLAN assignment.
- Host Isolated Access Port (I-Port): This port is associated with an Isolated VLAN and can only communicate with P-Ports.
- Host Community Access Port (C-Port): This port is associated with a Community VLAN and can communicate with P-Ports and all other C-Ports within the same VLAN.
In a real-world environment, multiple interconnected switches would likely be present. Additionally, the network gateway is often a firewall that may not be VLAN-aware.
From an operational standpoint, it is highly recommended to use switches of the same model and automate the PVLAN configuration to minimize human error.
Continue reading the post on Patreon .