EVE-NG Linux VM SSH troubleshooting
September 20, 2025
Industrial network segmentation with VLAN Insertion
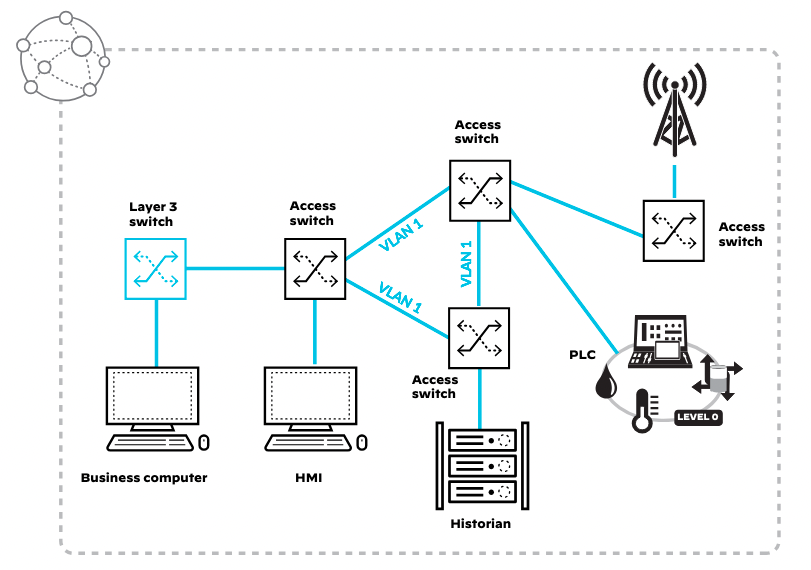
In real-world industrial environments, it is common to have all OT/ICS devices configured with IP addresses belonging to a single large network. This setup allows different production lines or plants to potentially communicate without any filtering.
Additionally, user PCs are often part of the same network for various purposes. Unfortunately, these PCs are more susceptible to malware due to inconsistent adherence to corporate policies. A malware infection within an OT/ICS network can easily spread due to weak security defenses.
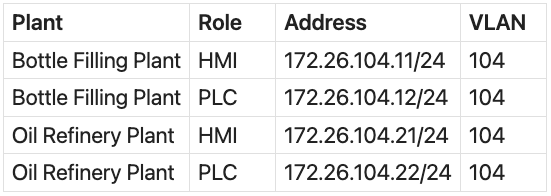
Our laboratory implements two different plants: the Bottle Filling Plant and the Oil Refinery Plant. In our setup, these two plants should not communicate with each other, even though they reside on the same IP network.
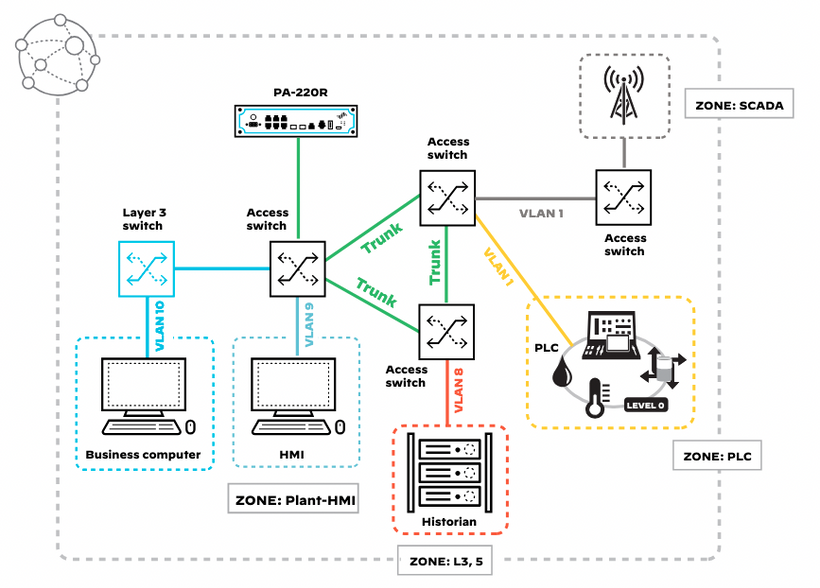
The goal is to segment the OT/ICS network transparently, minimizing disruptions.
Observations after VLAN insertion implementation:
- No IP address changes required
- Minimal downtime
- Increased network visibility
- Clear separation between IT and OT resources
- Ability to apply customized policies to different zones
- Capability for deep packet inspection on a per-zone basis
- Faster identification and isolation of potential issues
- Scalability up or down as needed
Grouping OT/ICS Devices Without Reconfiguration
Our laboratory includes the following devices:
Continue reading the post on Patreon .