EVE-NG Linux VM SSH troubleshooting
September 20, 2025
Ansible parsers and filters
The method we are using with Ansible is called “screen-scraper”, meaning the interaction with the device is not done through APIs but via CLI, emulating human activity. While this approach might be straightforward when typing commands, reading the outputs can be particularly challenging.
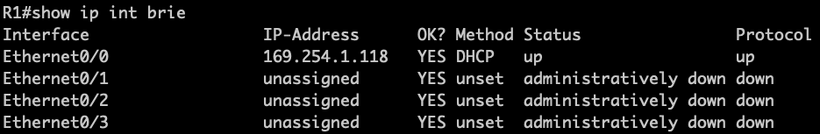
Consider the following output:
The above output is readable by humans but requires some work to be usable in a program. For instance, if we wanted to read the IP address of the Ethernet0/0 interface, we would need to search for the line where the interface name appears and then move a certain number of characters until we encounter the IP address. However, this is the format used by the Cisco IOS device in this example. If we change vendors or, in some cases, versions, the format of the table might change.
Parsers in Ansible handle this task: they read a text and convert it into a data structure. Parsers, essential unless working with APIs, are available for various types of text .
Regarding the topic we are addressing, we will look at four of them:
- TextFSM
- NTC Templates
- PyATS / Genie
- TTP
For our tests, we will use the “Simple Network Lab” environment, with R1 already running and reachable.
TextFSM
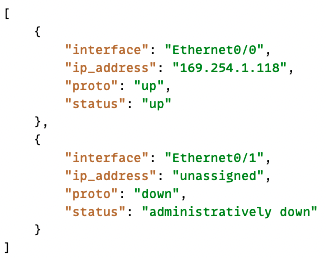
TextFSM , explored in a module of the basic course, is a module that reads a text and transforms it into a list of dictionaries. For example, the following text:
Can be transformed into:
Writing a template for TextFSM, at first glance, may not be simple, but once understood, it is not so complex. In this course, we limit ourselves to using existing templates, and in particular, we will refer to the NTC Templates repository. Let’s retrieve the template for the show ip interface brief command on Cisco IOS devices.
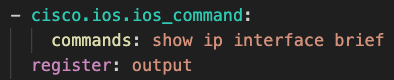
Now, we need to write a short playbook to connect to the device, issue the show ip interface brief command, and save it in a variable. The task is as follows:
Continue reading the post on Patreon .