Ansible Workbook
April 27, 2024
Approaching OT/ICS Cybersecurity
A few days ago, together with Rocco Sicilia and FESTO Academy , I presented a webinar on OT/ICS Cybersecurity approach. We are often spending time increasing Cybersecurity awareness, and that webinar was focused to gives Cybersecurity fundamentals to OT managers.
Understanding the Attacker’s point of view
The main discussion was about the Threat Actors, I mean, the attackers. Understanding the attackers gives us the big picture about the different business models they have (the “why”, using a definition by Simon Sinek ). We focused on:
- the evolving Cybercrime phenomena;
- the value the attacker is looking for;
- types of attackers, goals, and budgets;
Then we discussed some popular Cyberattacks: from WannaCry and NotPetya (2017) which I consider IT attacks to OT/ICS specific attacks: Stuxnet (Iran, 2010), BlackEnergy (Ukraine, 2015), Triton (Saudi Arabia, 2017), Florida city’s water supply (2021), Colonial Pipeline (2021), and the recent Viasat attack (2022).
Even if IT and OT attacks have different targets, we reviewed how attackers are used to breach in enterprises: three out of four Threat Vectors are based on human behavior, one Threat Vector only is technology-based.
Why (do we interconnect critical devices to Internet?)
Based on the previous paragraph the question is legitimate and the answer is obvious: the Industry 4.0 era is based on fast and automatic interactions (data exchanges). Data can be automatically transmitted between components, plants, systems, suppliers, customers… The more automatic and fast the process is, the more profitable the business is.
Cyberspace provides tools, methods, and interactions to get more opportunities.
But at the same time:
It is considered the fifth theater of warfare.
Place ourselves out of Cyberspace or interconnecting everything without considering the consequences are extreme solutions. We need to find the right balance between them.
Find the correct proportion between freedom, even unconscious, and security
Peculiarities of OT/ICS devices
The next chapter was about OT/ICS peculiarities. The audience was already aware, but we presented them from an IT perspective:
- designed for “availability”: the same term is used in the IT world with a different meaning;
- extremely sensitive to Ethernet disruptions and overloads: remember that Ethernet networks can fail by design (STP convergence);
- communications do not guarantee confidentiality, integrity, and availability: those are fundamentals attributes in IT security;
- long term life: compared to the IT world, we can see plants 20 years old;
- not subject to the same life cycle as IT components: production OT/ICS components (including HMI) are usually “untouchable”.
Based on our experiences, we presented seven common issues:
- Shadow OT: nobody knows exactly what is installed in plant networks and why (e.g. WiFi networks, cloud base telemetry, vulnerable devices, default passwords, remote access devices…). That leads to unmanaged Risk.
- Weak and sensitive protocols: OT/ICS protocols don’t follow the CIA triage used in IT, but they run on Ethernet networks. That leads to unexpected behaviors.
- Long term life devices: 5 years old plants installed and not maintained are vulnerable to well-known attacks. OT/ICS plants tend to be Legacy, weak and harmful.
- Remote maintenance: remote 3rd party operators can connect to critical plants anytime and acts locally, watch sensitive production processes and information (espionage and sabotage).
- Removable storage: 3rd party operators are used to upgrading software via untrusted USB keys. It’s not uncommon that malware spread via USB even today.
The list is not intended to be complete, of course; those are the main issues that industries are reporting to us.
How (should we approach Cybersecurity in OT/ICS environments?)
Without reinventing the wheel, there are many standards and frameworks which can be used: Framework for Improving Critical Infrastructure Cybersecurity (NIST) , CIS Controls , UNI ISO 31000:2018 Risk management — Guidelines, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations ( 800-171 and 800-172 ) and Secure Architecture for Industrial Control Systems (Purdue Model) were discussed during the webinar.
Special mention for the IEC62443 standard: it should be taken into account for both integrators and customers. Even if we still don’t have regulations for medical and industry sectors, IEC62443 is supposed to be a sort of guideline.
The purpose of this phase is to plan a strategy taking into accounts
What (should we do in practice?)
Cybersecurity is a process and is implemented with organization and technical measures. In practice we want to build a continuous improvement process, starting from the first major issue: Shadow OT.
We cannot protect what we don’t know.
The first step requires assessing the OT/ICS infrastructure, and finding out what is installed, the purpose, the business impact, the weakness or robustness… Then we can move on to the supplier, partners, 3rd parties, and employees and evaluate the Cybersecurity risk.
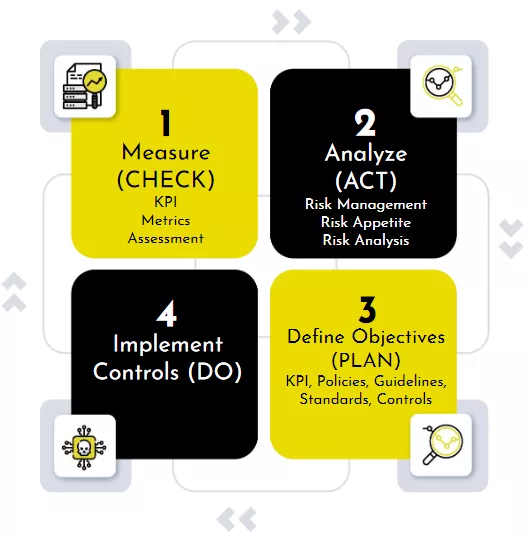
We can suppose a 4-phases improvement process:
- Check: measures the Cybersecurity posture (get qualitative or quantitative values regarding the many Cybersecurity aspects).
- Act: analyze the associated Risk and highlight the unacceptable ones.
- Plan: define a strategy to mitigate the unacceptable risks, taking into account standards and regulations.
- Do: govern and supervise the implementation.
It’s a PDCA cycle, but I’m starting from the third phase because I assume the first two steps are already been completed during the first iteration. It is expected that the next CHECK phase will get better KPI (Key Performance Indicators).
IT - OT Convergence
An interesting discussion was about IT and OT convergence: should we go for it?
I consider IT and OT two different worlds with different values and rules. In my opinion, they cannot converge and they shouldn’t. If IT guys follow the CIA (Confidentiality, Integrity, Availability) triad, the OT guys are following a sort of Safety, Reliability, and Productivity triad. Moreover, if uniqueness is something to avoid in IT (we don’t want to reinvent the wheel), customization is expected in OT/ICS.
But the IT and OT Cybersecurity must converge. Moreover, Cybersecurity must be a common overlay for all organization departments. The IT and OT Cybersecurity convergence point is defined by:
- Safety first.
- A Risk-based approach.
- Open mindset and dialogue with stakeholders.
Conclusions
Preparing a webinar or a training path is a good way to review concepts and organize them in a coherent flow. I hope auditors could get a different point of view regarding OT/ICS security. Slides are available and the additional session will be delivered in the future.