Ansible Workbook
April 27, 2024
Write-up Attacking ICS Plant 2
This post explore my second TryHackMe room: Attacking ICS Plant #2 . Because the VM can be unresponsive, I also provide the OVA for offline labs.
The room allows attacking a simulated refinery plant, gaining basic knowledge on ICS protocol weakness.
Task 1
The Attacking ICS Plant #1 room (get the offline version) is a prerequisite: complete it and download example scripts from there.
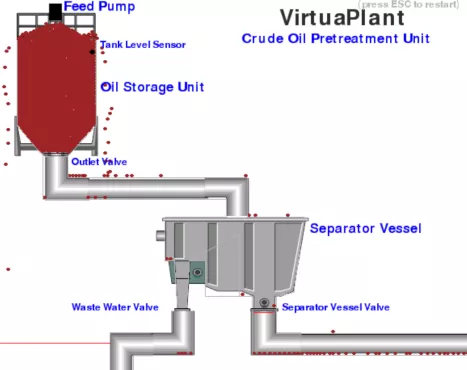
The first task requires understanding how the plant works. Use the discovery.py script and see how registries change.
We can observe:
- when the feed pump is filling the oil storage unit, registry 1 = 1 (PLC_FEED_PUMP);
- when the oil storage unit is full, registry 2 = 1 (PLC_TANK_LEVEL);
- when oil flows to through the outlet valve, registry 3 = 1 (PLC_OUTLET_VALVE);
- when the water flows out, registry 8 = 1 (PLC_WASTE_VALVE) and registry 6 increases (PLC_OIL_SPILL);
- when the oil flows out, registry 4 = 1 (PLC_SEP_VALVE) and registry 7 increases (PLC_OIL_PROCESSED);
Task 2
The solution requires opening the feed pump while maintaining closed the outlet valve:
- registry 1 = 1 (PLC_FEED_PUMP)
- registry 3 = 0 (PLC_OUTLET_VALVE)
Modify an attack script and run it. After 60 seconds, get the flag1: http://MACHINE_IP/flag1.txt.
Note: reset the plant by pressing the ESC button before starting the attack.
Task 3
The solution requires opening the feed pump, the outlet valve, and the separator vessel valve while maintaining closed the wastewater valve:
- registry 1 = 1 (PLC_FEED_PUMP)
- registry 3 = 1 (PLC_OUTLET_VALVE)
- registry 4 = 1 (PLC_SEP_VALVE)
- registry 8 = 0 (PLC_WASTE_VALVE)
Modify an attack script and run it. After reaching registry 7 > 1000 while registry 6 < 2, get the flag2: http://MACHINE_IP/flag2.txt.